When you hear about Tor, you might immediately think of the dark or deep web, filled with criminals, pornography, drug dealers and hackers. However, it might surprise you to know that Tor has a much more useful utility, and to those who care about it view the deep or dark web as a derogatory term, precisely because of those bad connotations of hackers and illegality.
Cybelle had come from Brazil to talk about Tor, try to explain how it worked, and dispel some of those misconceptions.
The first thing to know is what Tor stands for. The name Tor is derived from the acronym ‘The Onion Router’, but is styled as Tor, never TOR. It’s a free and open source software that is used to circumvent censorship, surveillance and tracking.
Initially built by the US Navy Research Lab, Tor is now maintained by The Tor Project, Inc., a non-profit organisation based in Seattle, Washington. Far from promoting illicit activity, The Tor Project’s mission is ‘To advance human rights and freedoms by creating and deploying free and open source anonymity and privacy technologies, supporting their unrestricted availability and use, and furthering their scientific and popular understanding.’
You can access it through the Tor browser, which is a security layered version of Firefox.
How does it work?
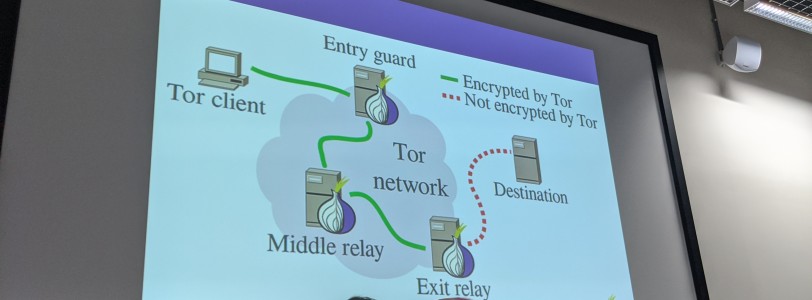
Tor a decentralised network that allows you to use the internet with as much privacy as possible.
It isolates every site you visit so that third party crawlers and advertisers can’t follow you around. Cookies and records in your browsing history are automatically deleted when you close your browser. It also prevents people monitoring your connection and discovering what websites you visit. They can only see that you’re using tor, nothing beyond that.
You open the Tor client, which then connects to the entry guard. You can then search the internet, and your requests get encrypted and sent to 3 separate servers (known as relays), and each one encrypts the data again, before reaching the final destination. Everything between the Tor client and the final relay is encrypted, and each relay is aware that traffic is coming from the node before it, but not the point of entry.
Your IP and location is masked making it very hard for ads and censorship to effectively work. The end-to-end encryption also makes it hard for people to intercept your traffic, and there is no single point of failure – an important distinction to simply using a VPN.
Sites you visit on Tor may have a sequence of 56 numbers and letters followed by .onion. This means that it is on the onion network, and isn’t available to access on the normal internet, which is why they’re known as the deep web. These sites don’t require HTTPS as they never leave the onion network, and the connection never leaves to the ‘insecure’ internet. You don’t have to buy a domain name on the .onion network, as addresses are automatically generated.
All tor browsers look the same, so it’s difficult to fingerprint based on browser size or OS, and Sites won’t know who you are UNLESS you log in.
The browser comes with HTTPS Everywhere and NoScript installed by default, and they encourage you not to add other plugins, as each additional plugin creates a new vulnerability that could risk compromising your data.
Why use it?
As stated above, the key benefits of Tor is to circumvent surveillance or censorship, especially in countries where the internet is not free. But, wider than that, it just helps to keep your data safe.
The internet economy is based on big data, advertising and non-consensual tracking. What that means is that advertisers are granted access to your data as you browse around the internet, either to display adverts to you, or be collected by data-brokers who then sell it on.
Tor allows you you mask your identity by hiding the file data and related meta-data, and makes your traffic look the same as everyone else’s as far as possible so you cannot be fingerprinted.
Equally, if you are in a country where the internet is censored or monitored, using Tor will provide you a degree of anonymity. That only extends so far though. For example, if you start logging into Google, or Facebook, those websites will know that you have logged in, and you are then no longer afforded anonymity.
How do I use it?
Getting Tor is exceptionally easy!
You can download the browser directly from the website, use a mirror, or email, or DM on Twitter with your OS and two letter language code.






0 Comments